時間:2024-03-28|瀏覽:945
Late on Tuesday night, the crypto community witnessed another breach. Ethereum Layer-2 NFT gaming platform Munchables reported that it was attacked on an X post.
The cryptocurrency heist, which at one point stole more than $62 million, took a shocking turn when the identity of the attacker was revealed.
Cryptocurrency Developer Turns Hacker
Yesterday, Blast-powered gaming platform Munchables suffered a security breach that resulted in the theft of 17,400 ETH worth approximately $62.5 million. Shortly after this X announcement, crypto sleuth ZachXBT revealed the amount stolen and the address to which the funds were sent.
It was later revealed that the crypto theft was the work of an insider rather than an outside attack, as one of the project's developers appeared to be the culprit.
Solidity developer 0xQuit shared worrying information about Munchable on X. The developer pointed out that the smart contract poses a serious security risk because it is a proxy contract that can be upgraded, but its implementation contract does not need to be verified.
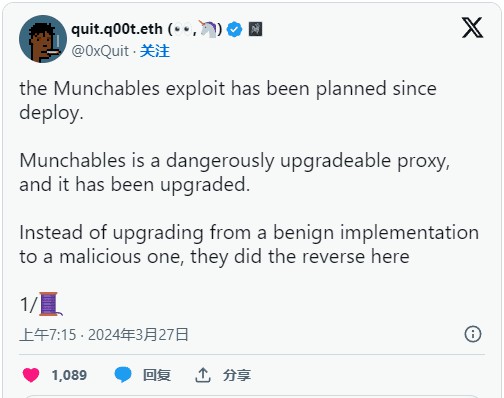
The vulnerability does not appear to be complex, as it involves claiming stolen funds from the contract. However, it requires the attacker to be an authorized party, which confirms that the theft was a conspiracy orchestrated within the project.
0xQuit conducted an in-depth investigation and concluded that the attack had been planned since its deployment. The developers of Munchable took advantage of a feature of smart contracts, which is that contracts can be updated and upgraded. In the process, the developer secretly set himself a huge ether balance before replacing the implementation of the contract with a ostensibly compliant version.
When the total value locked (TVL) is high enough, the developer “simply withdraws the balance.” Data from DeFiLlama shows that before the breach, Munchables’ TLV was $96.16 million. As of this writing, TVL has plummeted to $34.05 million.
As BlockSec reported, the funds were sent to a multi-signature wallet. The attacker eventually shared all private keys with the Munchables team. These keys provide access to $62.5 million worth of ETH, 73 WETH, and owner keys containing the rest of the project’s funds. According to calculations by Solidity developers, the total amount is close to $100 million.
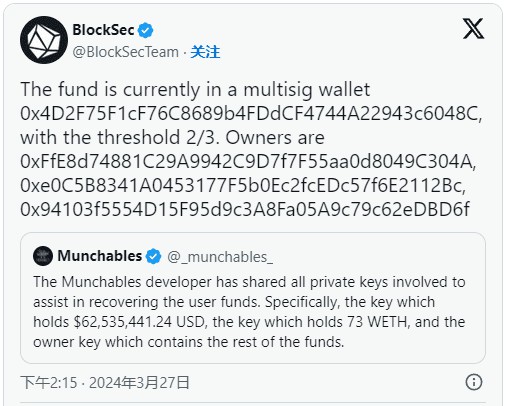
Changing attitudes or fear in the crypto community?
Unfortunately, encryption breaches, hacks, and scams are common in the industry. Most of the time, hackers walk away with huge sums of money, leaving investors with empty pockets.
This time, the events are even more thrilling than usual, as the developer takes on the identity of a hacker, uncovering a web of lies and deception. As ZachXBT suggests, Munchable's renegade developer appears to be North Korean and appears to be associated with the Lazarus group.
However, the movie doesn't end there: Blockchain investigators revealed that four different developers employed by the Munchables team were all related to the exploiter, and they all appear to be the same person.
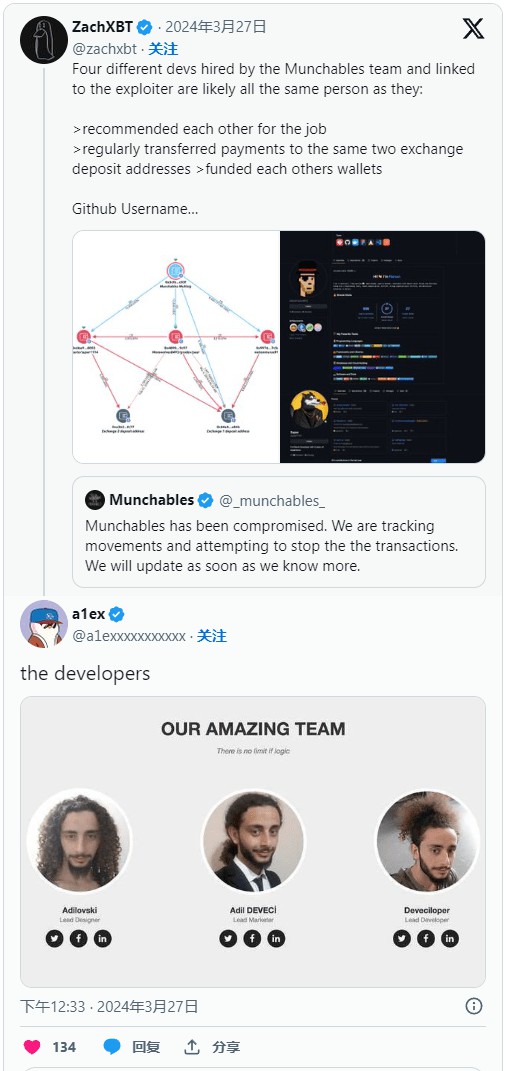
These developers recommended each other for the job and regularly transferred payments to two different deposit addresses on the same exchange to fund each other's wallets.
Journalist Laura Shin raised the possibility that these developers may not be the same person, but different people working for the same organization: the North Korean government.
The CEO of Pixelcraft Studios added that he has offered the developer a trial hire in 2022. In the month the former Munchables developer worked for them, he exhibited "very suspicious" behavior.
The CEO believes a link to North Korea is possible. Furthermore, he revealed that the operating model at the time was similar to this incident, as the developer tried to get his "friend" to be hired.
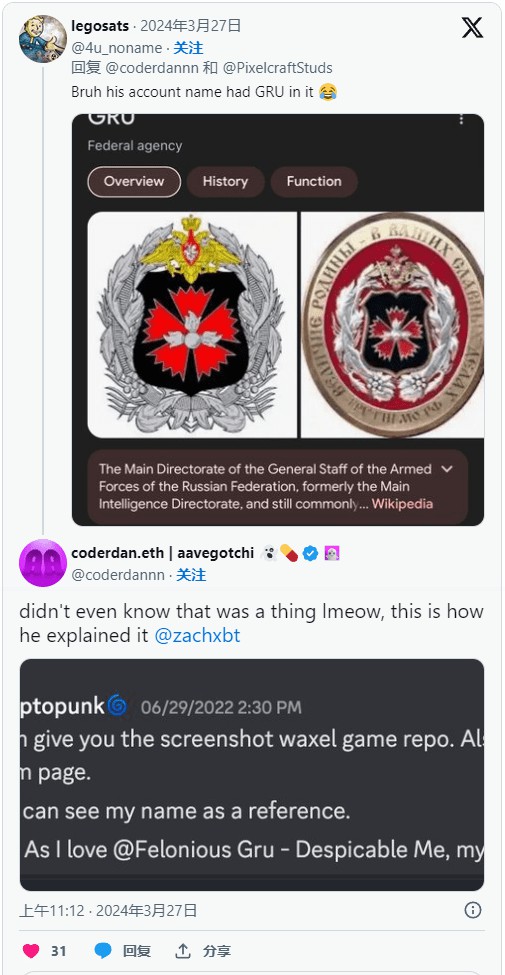
An X user highlighted that the developer's GitHub codename is "grudev325" and pointed out that "gru" may be related to the Russian Federal Military Intelligence Service.
Pixelcrafts' CEO commented that at the time, the developer explained that the nickname came about after his love for the Gru character from the Despicable Me movies. Ironically, the character is a supervillain who spends most of his time trying to steal the moon.
Whether he was trying to steal the moon or failed like Gru, the developer ultimately returned the funds without asking for "compensation." Many users believe that this suspicious "change in attitude" is due to ZackXBT's penetration into the attacker's web of lies and warnings.
The thriller ended with a response from a crypto investigator to a now-deleted post. In his reply, the detective threatened to destroy the developer and "other North Korean developers" and said "your country will face another blackout." #安全漏洞 #Munchables
熱點: IN